
Red Team Exercises
and Adversary Emulation
Active Cyber Defense
What is Red Team Exercises and Adversary Emulation
Traditional vulnerability assessments and penetration tests are an important way to assess the security posture of your organization’s IT networks, looking for vulnerabilities and exposures that can be leveraged as targets of opportunity by a wide range of attackers. However, these types of assessments alone do not adequately simulate attacks from dedicated adversaries who are intent on breaching your network. During an adversary emulation, or red team exercise, our security experts will launch a realistic attempt to exploit your environment to gain access to systems that would enable us to impact the critical functions necessary for your operations.
How it works
This simulated attack is carried out in a controlled manner to ensure that your operations are not adversely affected, while still providing valuable information regarding gaps in your preventive or detective controls that could allow an adversary to harm your organization. The attacks utilize real-world adversary tactics, techniques and procedures (TTPs) that represent a genuine threat to the critical functions of your organization.
Adversary emulation exercises provide visibility into the business impact of gaps in your network security. While a series of medium risk vulnerabilities may be identified during a traditional vulnerability assessment / penetration test, if those vulnerabilities can be combined into an effective attack chain that results in significant compromise of the organization, then their impact is critical. Adversary emulation exercises demonstrate the risk that real-world threats represent to the organization.
Adversary emulation exercises provide visibility into the business impact of gaps in your network security. While a series of medium risk vulnerabilities may be identified during a traditional vulnerability assessment / penetration test, if those vulnerabilities can be combined into an effective attack chain that results in significant compromise of the organization, then their impact is critical. Adversary emulation exercises demonstrate the risk that real-world threats represent to the organization.
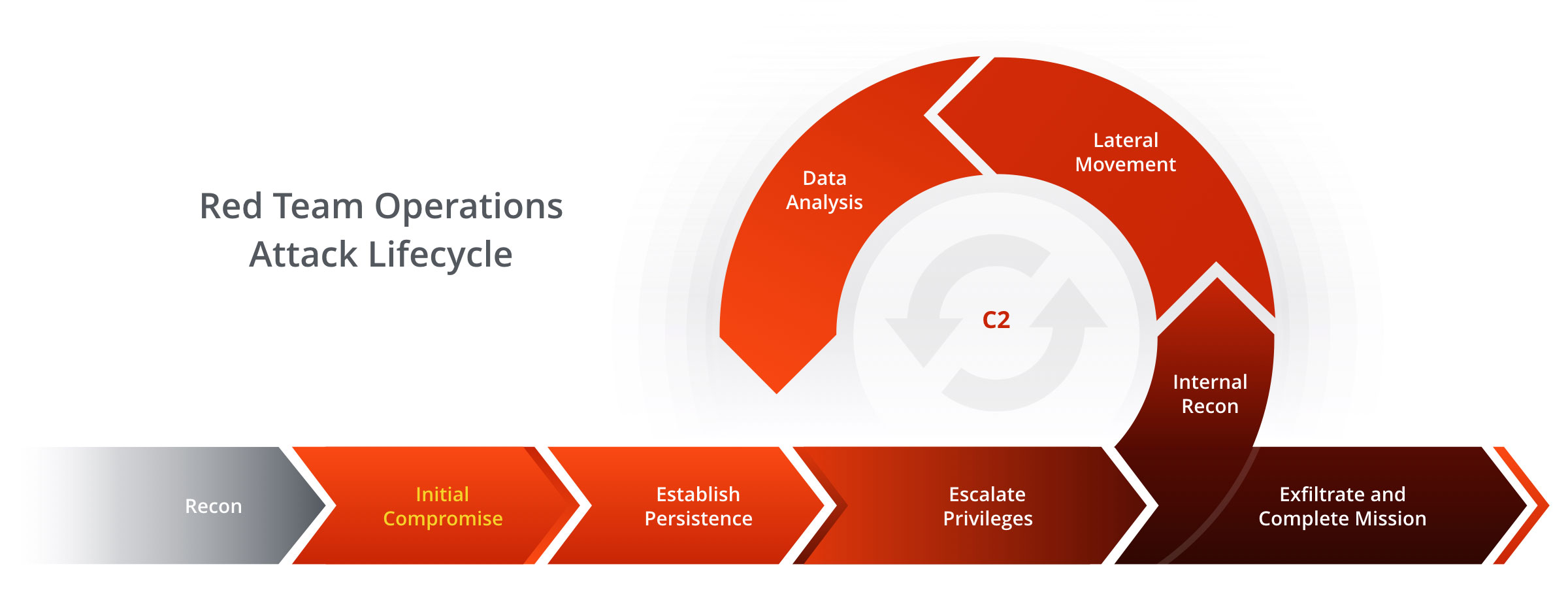
Each adversary emulation exercise begins by analyzing available threat intelligence regarding adversaries who may actively target your organization and the TTPs that such adversaries would be likely to leverage.
The sources of intelligence used will vary from client to client but will always include industry-standard information such as MITRE’s ATT&CK Matrices and other open source intelligence related to global and regional threat actors and the tools and techniques they utilize. Our team will also perform open source intelligence collection and reconnaissance to create a target profile of your organization.
The sources of intelligence used will vary from client to client but will always include industry-standard information such as MITRE’s ATT&CK Matrices and other open source intelligence related to global and regional threat actors and the tools and techniques they utilize. Our team will also perform open source intelligence collection and reconnaissance to create a target profile of your organization.
Based on collected threat intelligence, our team will devise a series of attack scenarios against your critical functions. Using the agreed-upon tactics, techniques, and procedures aligned to those likely to be used by real-world threat actors, our team of security experts will conduct an offensive campaign against the identified critical functions of your organization.

In addition to identifying gaps in your network security posture, these exercises also improve the visibility and capability of your network defenders. At the end of each adversary emulation, our team will work with yours to ensure that all attack techniques leveraged against your organization are clearly explained, evidence that may have been left behind is identified, and suggestions for improving controls to prevent or detect similar attacks in the future are provided. Adversary emulation exercises should be done on a periodic basis to assess and improve your overall network defense.
Explore all our services

Telecommunications Security
Talk to a Forward Defense Security expert today
Is your business secure? Complete the meeting schedule form to talk with a Forward Defense Security expert about your compliance and security needs.
Get a quote




