
Cyber Deception
Active Cyber Defense
What is cyber deception
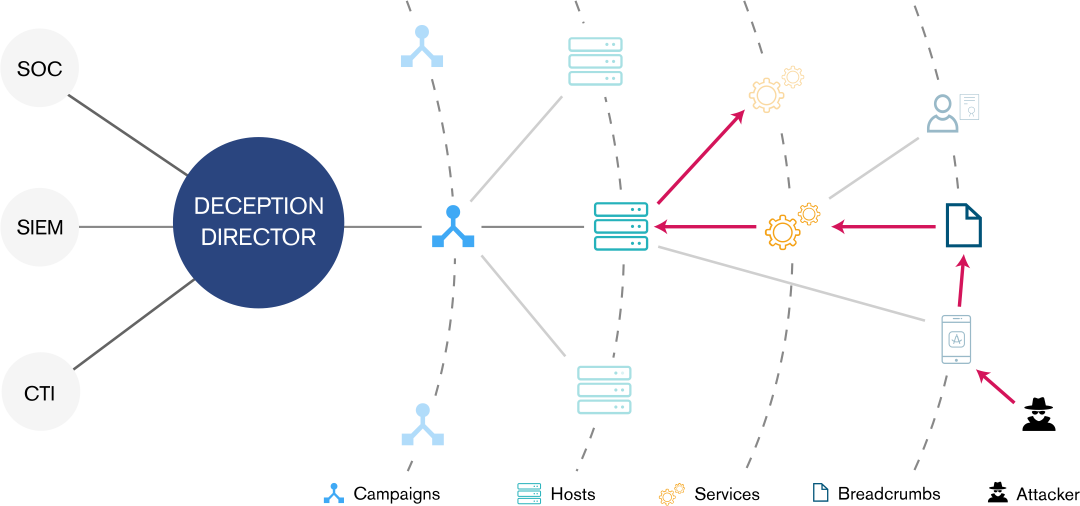
Cyber deception refers to taking steps to confuse and draw out attackers within your environment. By placing a variety of false flags throughout your organization, adversaries can be detected when they interact with those systems while moving through and enumerating the systems in your environment. Cyber deception is not a replacement for good IT security hygiene; however, it can provide an effective means of identifying adversaries that were previously undetected inside of your networks and allow you to launch an effective response to mitigate the damage caused by their presence.
Cyber deception can take a variety of forms:
Honeypots
Both low interaction and high interaction, can be placed within the environment and monitored for activity. These systems have no legitimate business purpose and should never be interacted with by your employees, so any connection to these systems is suspicious and warrants further investigation. This concept can be extended to honey accounts, privileged accounts that are not actually used within your environment and heavily monitored for attempted use by adversaries.
Honey credentials
Seemingly valid administrator credentials placed in memory to detect the use of credential reuse attacks, and similar variations on this theme can likewise be effectively deployed to discover malicious actors within your environment.
In addition to improving detection, cyber deception techniques can also be leveraged to confuse and disorient an adversary who may gain a foothold inside your environment. Attackers must perform enumeration and discovery of systems and data of value inside of your environment. Cyber deception techniques can be applied to make this task more difficult, provide false readings to the adversary, and slowing their progress when they attempt to identify data of value in your organization. By forcing them to expend more time and resources to achieve their intended objectives, you increase your opportunities to detect and respond to the threat.
Forward Defense can help you design a cyber deception program, leveraging commercial or open source products, to best meet the needs of your organization.
Forward Defense can help you design a cyber deception program, leveraging commercial or open source products, to best meet the needs of your organization.

Explore all our services

Telecommunications Security
Talk to a Forward Defense Security expert today
Is your business secure? Complete the meeting schedule form to talk with a Forward Defense Security expert about your compliance and security needs.
Get a quote




